Tightening Up Your Github Security
GitHub reconnaissance is a tactic attackers use to gather information about their targets. Attackers analyze an organization’s GitHub repositories and check for sensitive data that has been accidentally committed or information, potentially leading to the discovery of a vulnerability. Today, we'll take a look at how attackers research your GitHub repositories. By looking at these recon techniques, you can find out what is revealed through your GitHub repositories and what you can do to tighten up your GitHub security!
Analyzing GitHub Repositories
First, make a list of all GitHub repositories relevant to your organization. You should look at the GitHub repositories of your organization as well as the public repositories of your organization’s employees. A good place to start is searching for your organization’s name in GitHub to find relevant usernames and projects. For example, here are the search results of the term
okta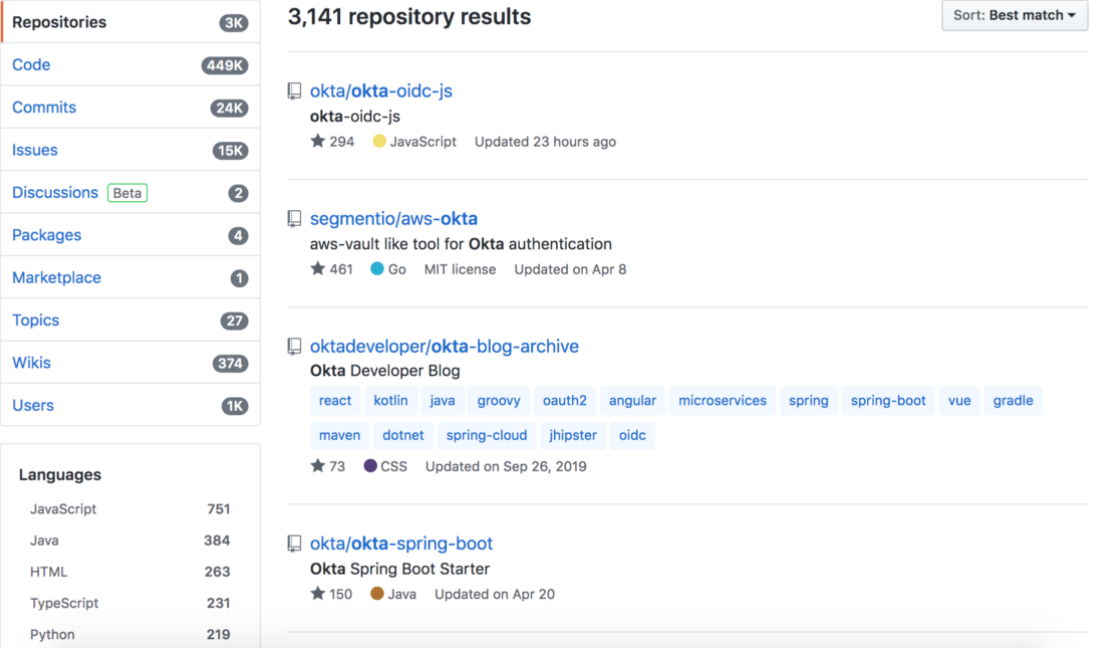
Once you’ve found the organizations or usernames you want to audit, visit their pages. After that it’s time to dive into the code! On the organization or user page, switch the search type to
Sources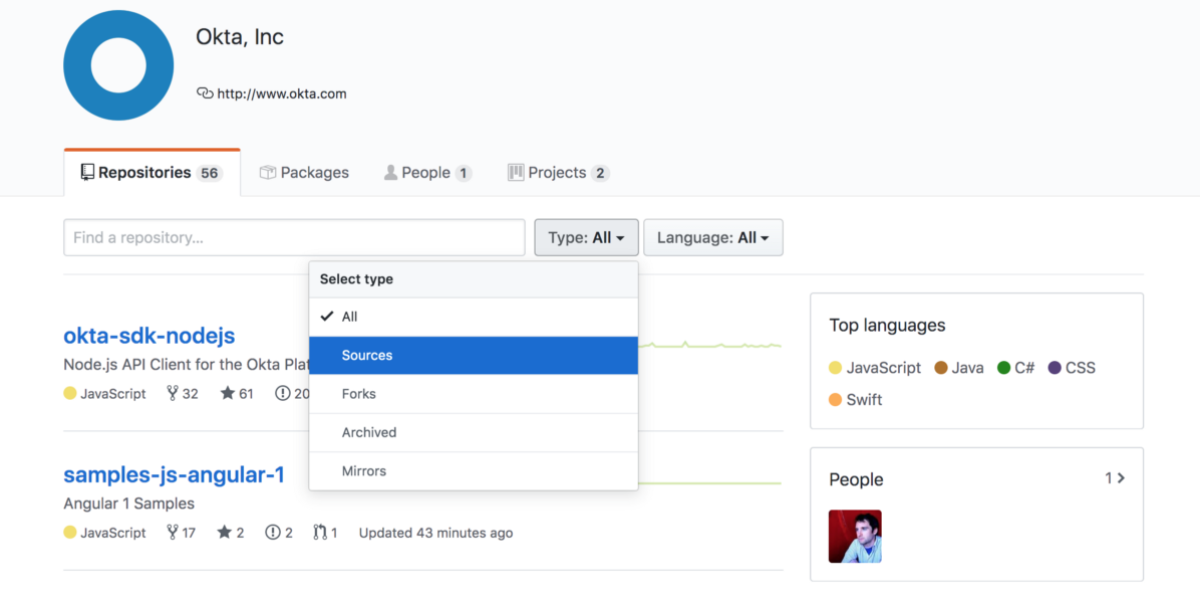
You can then focus your attention on a single repository and go crazy in the search bar! For each search result, pay special attention to the
issuescommits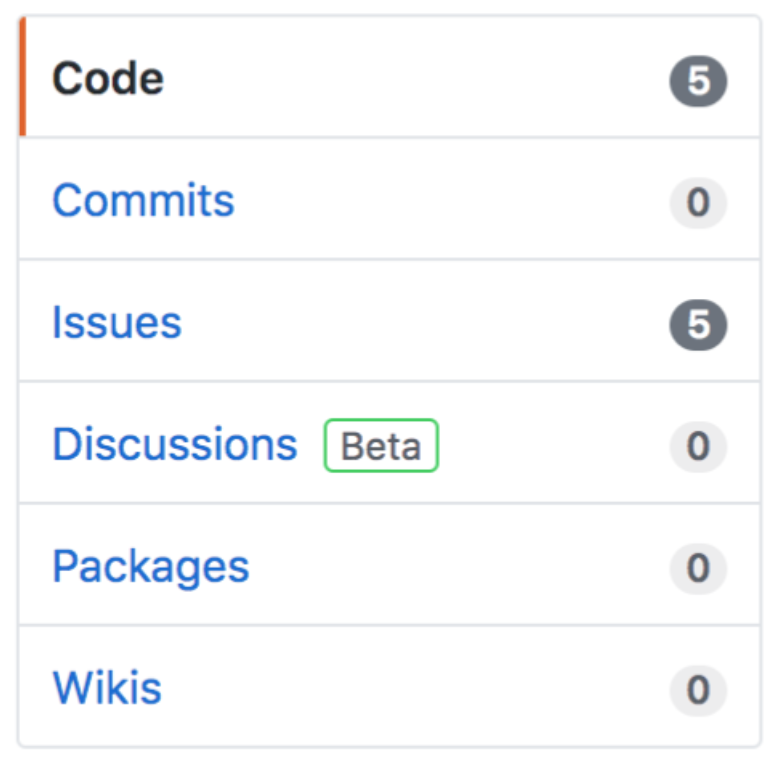
Then, turn your attention to the
code sectionblamehistory
How to Search for Vulnerabilities in GitHub Repositories
What search terms should you use to find potentially dangerous code efficiently? Here are a few things to look for when auditing your GitHub repositories.
Hardcoded Secrets
First, look for hardcoded secrets such as API keys, encryption keys, and database passwords. Some keywords that often find secrets are
keysecretpasswordencryptAPICSRFrandomhashMD5SHA-1SHA-2HMACapi_keysecret_keywas_keyFTPloginGitHub_tokenSensitive Functionalities
Next, you should search for the sensitive functionalities in the project. Focus on important functions such as authentication, password reset, state-changing actions, and sensitive info reads. Then, review how these components interact with other functionalities. You can use the search terms
authauthenticationpasswordpasslogininputfile_inputgetuser_inputURLparameterreadDangerous Functions and Outdated Dependencies
Outdated dependencies and unchecked use of dangerous functions are also a huge source of bugs. Search for dependencies being used and go through the versions list to see if they are outdated. Some search terms you can use are
importresourcesdependenciesinput()eval()Development Side-effects
Search for developer comments, hidden debug functionalities and configuration files. Developer comments can point out obvious programming mistakes, hidden debug functionalities often leading to privilege escalation, and config files allowing attackers to gather more information about your infrastructure. Search terms you can use in this category are
tododeprecatedvulnerablefixcompletedconfigsetuptododevdeprecatedvulnerableremovedHTTPHTTPSFTPWeak Cryptography
Finally, search for the use of weak cryptography or hashing algorithms. This is an issue that is hard to find during a black-box test, but is easy to spot when reviewing source code. Look for issues such as weak encryption keys, breakable encryption algorithms, and weak hashing algorithms. Search for terms like
ECBMD4MD5Automating Vulnerability Analysis for GitHub
If you are looking for a faster approach, you can use tools like Gitrob and Trufflehog to automate the GitHub recon process. Gitrob is a tool that finds potentially sensitive files that are pushed to public repositories on GitHub. You can find Gitrob here. On the other hand, Trufflehog specializes in finding secrets in repositories by searching for high-entropy strings. You can find Trufflehog on GitHub here.
Eliminating GitHub Security Holes
Now that you’ve identified your GitHub weaknesses, here are a few steps that you can take to tighten up your GitHub security. First, every piece of sensitive data exposed through a public GitHub repository should be considered leaked. Therefore, you should rotate every credential found in your repositories. Next, fix or patch vulnerabilities that you have found via code analysis. Again, these weaknesses should be considered public information and you should remediate them ASAP. Finally, remove any additional sensitive information from the repositories and commit histories!
